Understanding Business Email Compromise and Proven Prevention Strategies

Business Email Compromise (BEC) is a targeted attack that uses social engineering tactics to gain access to sensitive information or funds. Attackers often use impersonation techniques to pose as someone in authority, such as a CEO or a vendor, and then request sensitive information or payment. These attacks are often successful because they rely on trust and the victim's willingness to comply with the request.
It is important to note that security controls such as firewalls and spam filters may not stop these emails from being delivered because they typically do not contain a payload, such as malware. Instead, the email itself is the weapon.
To help you understand what a BEC email might look like, here is an example:
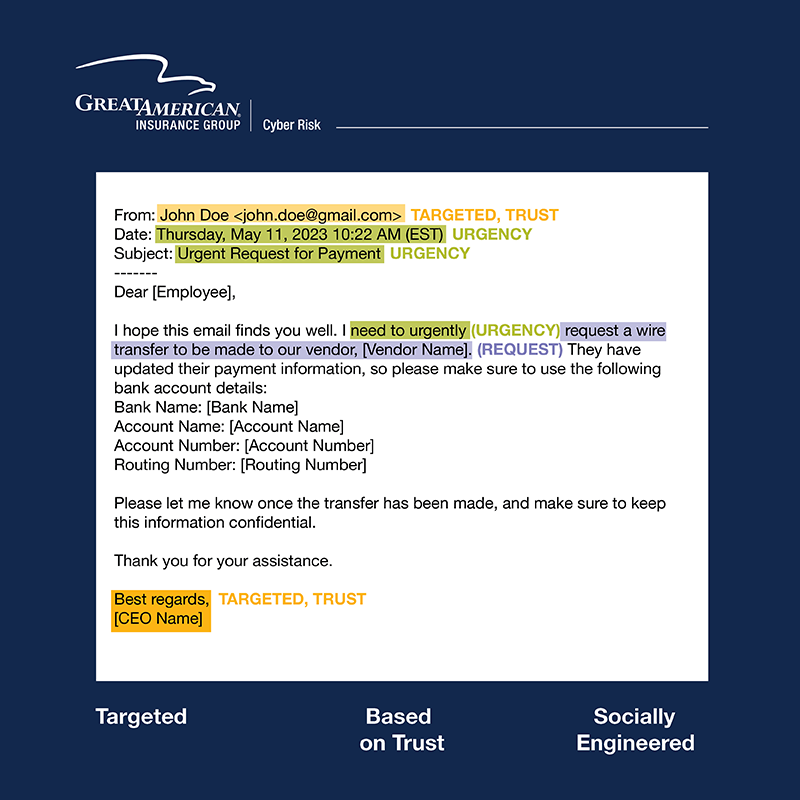
As you can see, this email appears to be from a trusted source, and it requests sensitive information and payment.
Business Email Compromise attacks are:
- Targeted: Cybercriminals will spend time researching a business, it’s executives, and their clients, to identify the recipient of an attack for the greatest chance of a successful campaign.
- Built on Trust: Attackers will pretend to be a friend, employee, or vendor, sharing/requesting PCI or PII in the process of manipulating someone’s trust.
- Socially Engineered: The language used in these emails are specifically designed to trigger emotion, create a sense of urgency or fear, and may even provide context for why the email is being sent from a personal account.
- Absent of Malicious Payloads: because these emails are designed to elicit emotional responses, there need not be a malware infected attachment or link. This helps bypass any filtering software that has been installed on email servers.
Historically, BEC has been more easily identifiable due to misspellings, or in some cases, poor grammar from people who aren’t native English speakers. Recently, given the rise of AI and large language models, these email campaigns have become more difficult to detect and increasingly more frequent.
How to Prevent BEC Attacks
There are a few controls you can implement to mitigate this risk:
- Sender Policy Framework (SPF) which is an email authentication methodology that helps to identify the servers that are allowed to send emails for a domain.
- Domain Keys Identified Mail (DKIM) is an authentication protocol that detects forged sender addresses with the help of digital signatures.
- Domain-based Message Authentication, Reporting, and Conformance (DMARC) which tells the receiving server what to do with messages from your organization that aren’t authenticated using SPF and/or DKIM.
- Security Awareness and Training for individual contributors can help protect the company from loss due to human error.
If you receive an email like this, please be cautious and verify the request with the supposed sender using a different method of communication, such as a phone call. Remember, your company's security is everyone's responsibility, so please remain vigilant and report any suspicious activity immediately.
Help Secure Your Business with Cyber Insurance
Our experienced team of cyber risk professionals understands the complex digital threat landscape businesses operate in. Learn more about our easy-to-understand cyber risk products designed to meet the differing needs of different small and mid-sized clients.









